There has been known weaknesses with the various key less entry solutions among cat manufacturers, the debacle on the system used by JEEP springs to mind. Now we see a weakness in the Mercedes Benz solution. In a video released by the West Midlands Police in the UK we see thieves sniffing out the key code from the key inside of the house, and then transfers it to a sender by the car to open and start the car. Time to look at at NFC blocking key storage I suppose.
Month: November 2017
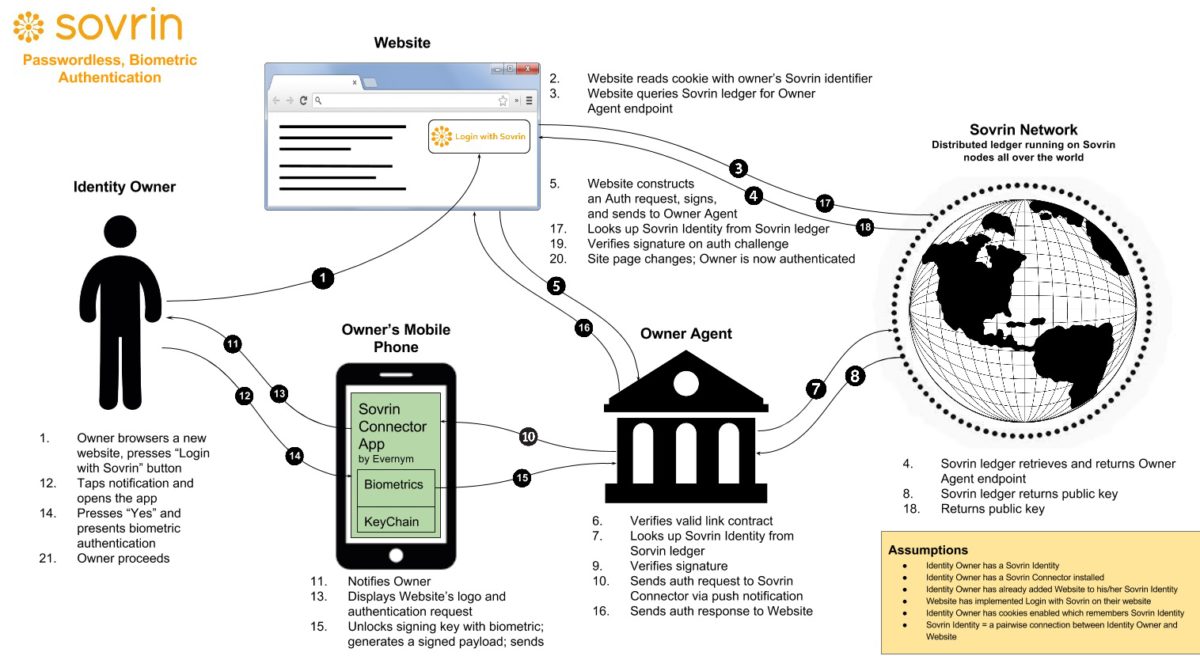
Digital Identities – an distributed approach
Traditional Digital identity schemes, such as the X509 certificate approach and similar, has always carried substantial overhead and cost to reach non-repudiation. With the explosion of distributed ledgers in areas such as digital currencies and the current reluctance by consumers on using IOT solutions due to privacy and security issues there is a need for an alternative. The Sovrin foundation has taken this and have made an “Self-Sovereign” Identity solution. Based on open-source distributed ledger technology this approach has a lot of potential, in particular in the theoretical ability to self manage devices and their trust relationships. The illustration here shows how this works in the real world.
Mass Surveillance is alive and kicking
Amazon S3 buckets belonging to American inteligense have been found open to the public by researchers from the Upguard Cyber Risk Team. 3 buckets, “centcom-backup,” “centcom-archive,” and “pacom-archive” (Centcom = American Military Central Command, Pacom = American Pacific command) represents 8 years of Social Media scraping with up to 1.8 Billion posts collected. Posts, users, IP numbers, password hashes etc all collected. Clues left leads to some information on the vendors involved and the tools used to analyze the data. Remember: nothing is private on Internet!
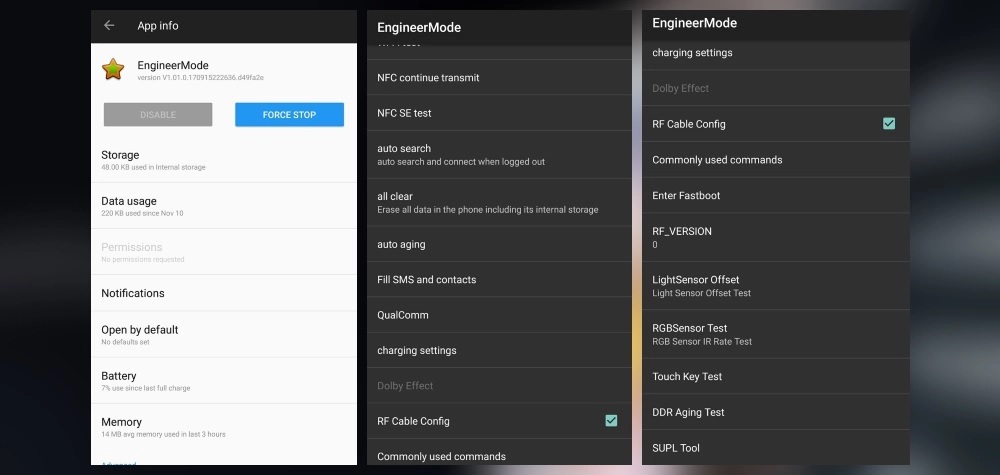
Note to Oneplus: Remember to clean up devices after QA
There has been a lot of discussions on the amount of data transmitted by Oneplus devices to the mother ship. A security researcher suing the monikor Elliot Alderson decided to dig deeper to find out what data was being sent. As he dug through the OS (OxygenOS) on his phone he discovered an EngineerMode app. This app (assumed to be an internal testing tool for QA) gives access to all aspects of the phone, including rooting. A quick check for Oneplus owners it to enter *#808# SSID, which will bring up the app if present. A hcak (for now) requires physical access.
Apple’s next exclusive TV content
Apple’s plans to enter the consumer media market have been know for long, and now more confirmed deals are public. The deal with Steven Spielberg on the resurrection of the Amazing Stories anthology has already been announced, now Apple has signed the right for 2 seasons of TV based on the Brian Stelter’s book ‘Top of the Morning: Inside the Cutthroat World of Morning TV “ and will star Jennifer Aniston and Reese Witherspoon.
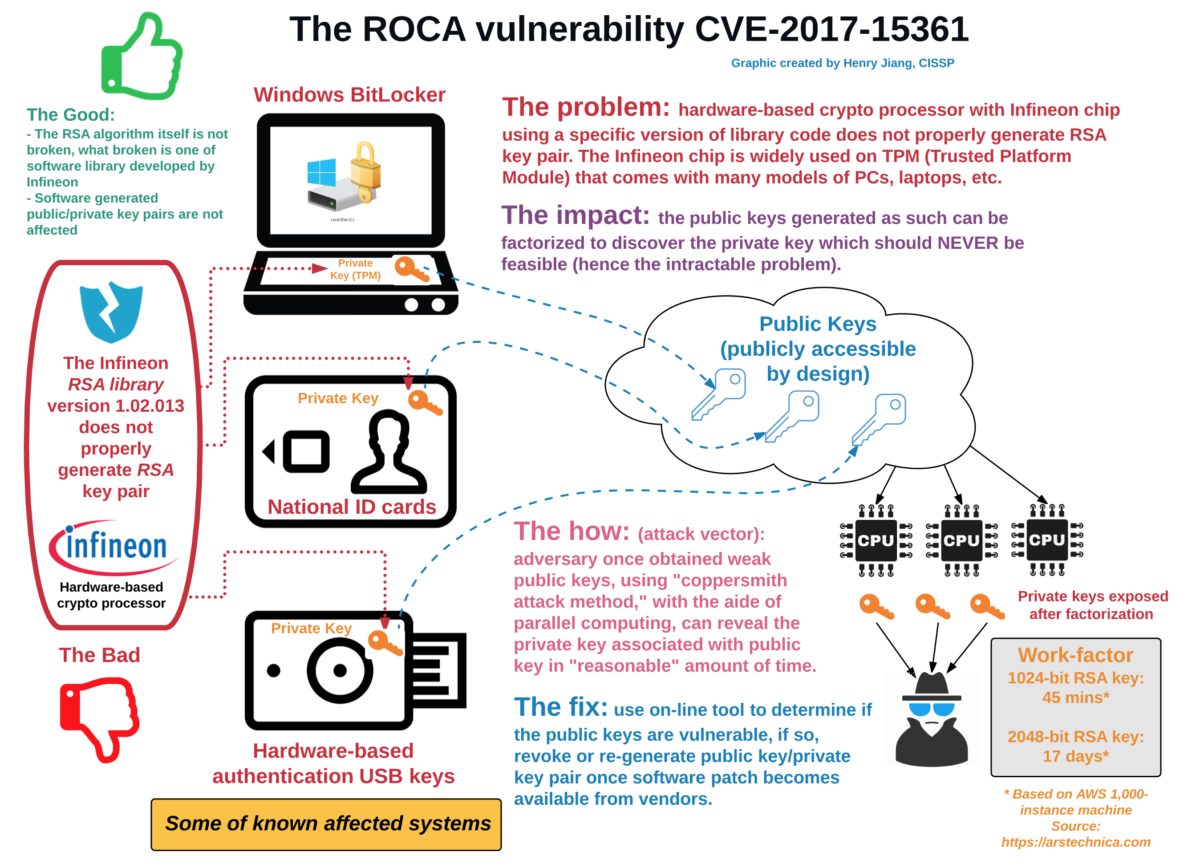
The Return of Coppersmith’s Attack
The Infineon-developed RSA Library version v1.02.013, arguably one the most commonly used libraries for RSA Prime Calculations in almost all major public PKI solutions has been discovered to contain a major flaw in the way the randomness of the keys are calculated. A study by Matus Nemec, Marek Sys, Petr Svenda, Dusan Klinec and Vashek Matyas shows that “…our discovery of an algorithmic aw in the construction of primes for RSA key generation in a widely-used library of a major manufacturer of cryptographic hardware. The primes generated by the library suffer from a signicant loss of entropy”.
This has had massive impacts, perhaps the most public is the cancellation of a major part of the current generation of National ID Cards in Lithuania. Remember that security without randomness is no security!
Facebook’s shadow profiles
Facbook’s People You May Know algorithm has been of interest for security minded people for a while. A number of “weird” and inappropriate suggestions has led to Gizmodo digging deeper into the underlying systems and approaches. In fairness, most of the approach is clearly highlighted in the respective EULA’s, but how many users actually reads them?
Another Crypto Currency Hard Fork?
Etherum (the most referred to competitor to Bitcoin currently) has had another “incident”. You may remember the USD 32 million USD hack on Etherum in July and the subsequent (heavily criticized) hard fork to zero out the hack. Now a “mistake” from a developer has locked down wallets worth USD 300 million. The attack relates to a quirk in Etherum’s multisignature wallets, and will most likely require another hard fork to rectify. Again a warning that crypto currencies are still evolving, in most cases at a slower pace than the money thrown at it.