As the world keeps on getting excited with IOT and the security (or lack thereof) is getting a lot of attention. Karl Marx famously stated that “History repeats itself, first as a tragedy, second as a farce” so a look at the same issues in current infrastructures such as remote terminal units (RTU) Programmable logic controller (PLC) and the latest discovery with the Ovarro RTU proves that the history like Stuxnet is an relevant exaple of the problems IOT will face.
Category: Mobile
[Updated] More Apple iOS source code leaks (iBoot)
Yet more Apple source code has been leaked, this time around the iBoot elements of IOS. Although from an older build of IOS (9x) it should be close to the current implementation. Initially leaked on Reddit by a user named apple_internals and subsequently removed, now posted in Github for maximum availability. An good article on Motherboard does some initial analysis and impact analysis. It’s a shame jailbreaking has gone out of Vogue, this will make it a lot simpler to do.
[Update] Apple has released the following statement” Old source code from three years ago appears to have been leaked, but by design the security of our products doesn’t depend on the secrecy of our source code. There are many layers of hardware and software protections built in to our products, and we always encourage customers to update to the newest software releases to benefit from the latest protections.”
A DMCA notice has been sent to Github to take down the source code.
Further Microsoft Patents: Is the Windows Phone back on?
I have mentioned a couple of times that keeping an eye on patent applications filed by Microsoft can give you a glimpse of things to come. Much like the surface book series was preempted by the key technologies patented, there is now more patent applications for the much debated Microsoft mobile terminal (sometimes referred to by the internal (?) project name Courier). A good summery in Arsthecnica, showing more and more of the expected device.
Note to Oneplus: Remember to clean up devices after QA
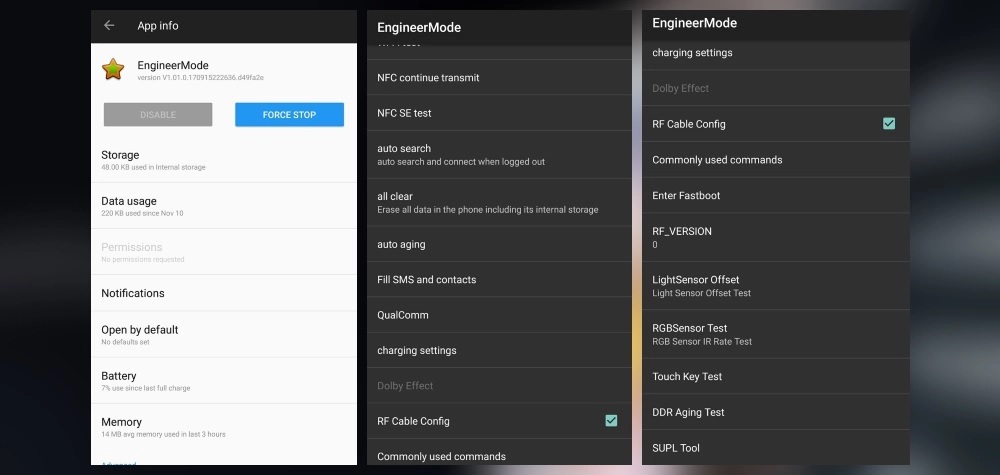
There has been a lot of discussions on the amount of data transmitted by Oneplus devices to the mother ship. A security researcher suing the monikor Elliot Alderson decided to dig deeper to find out what data was being sent. As he dug through the OS (OxygenOS) on his phone he discovered an EngineerMode app. This app (assumed to be an internal testing tool for QA) gives access to all aspects of the phone, including rooting. A quick check for Oneplus owners it to enter *#808# SSID, which will bring up the app if present. A hcak (for now) requires physical access.
KRACK: Key Reinstallation Attacks
Mathy Vanhoef and Frank Piessens of KU Leuve have discovered a critical flaw in the way WPA2 encryption for all known WiFi implementations. Some time to caveat on the width of the discovery, the attacker needs physical access to the network, and will only see non-encrypted transmissions. Until the vendors patch their implementations the only interim solution is to treat your home WiFi as you would a public WiFi, using HTTPS and in an ideal world VPN form the individual client.
This overview on Github shows the current state of fixes from the vendors. I somewhat sadly note that the majority of my HW is under the “No Known Official Response” category!
The cost of unlimited data plans on customers in the US
Opensignal has just released their “State of Mobile Networks: USA” for August of this year. The volumes created by the unlimited data plans are eating up the networks capacity, with less than ideal impacts in the users with ever depreciating speeds as an outcome.
This will at some stage have to be addressed, an yet another shot across the bow of Net Neutrality – We need a way to shape the traffic to enable a more satisfactory end user experience, and to let people pay for prioritized use. Can this lead to a final universal adaptation of IP6?
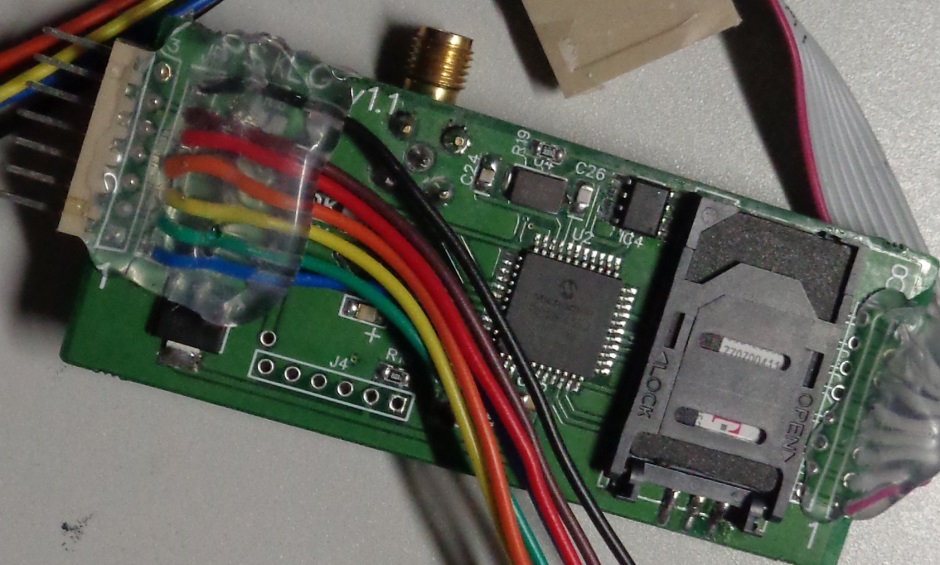
Skimming devices now call home
A new generation of mag-stripe skimmers with a fully built in GSM device has been found in US Petrol pumps, as shown in a recent article by Brian Krebs. The captured devices contained a common T-Mobile GSM SIM, allowing for the captured data to be immediately transferred via SMS to the skimmers for real time use and abuse. All of course down the the US slowness in implementing the Chip / PIN security aspects ot EMV.
Finally: battery levels on connected Bluetooth devices in Android
It looks like there will finally be a general introduction in Android of being able to see the battery status of any connected Bluetooth devise. This has been available in custom and manufacturers for a while, and plenty of options in the app store, but up until now this has been the landscape. An article on XDA finds that “we can see that Google will add a new method in the Bluetooth Device class called getBatteryLevel() ” in the proposed new Android Open Source Project (AOSP) release.

![[Updated] More Apple iOS source code leaks (iBoot)](https://www.solberg.co.uk/wp-content/uploads/2018/02/1518047804451-Screen-Shot-2018-02-07-at-63528-PM.jpg)